IVORY and its partners will attend NAB 2023 in Las Vegas

IVORY and its partners will be at NAB Las Vegas 2023
Between April 16 and 19, the NAB Show is a global gathering of content professionals from the media, entertainment and technology industries.
IVORY will be present to discuss and support visitors in their digital transformation challenges.
We are happy to represent the interests of Codemill, Embrace, iconik and Object Matrix in France, Belgium and Luxembourg.
Get in touch with our team to schedule a meeting!
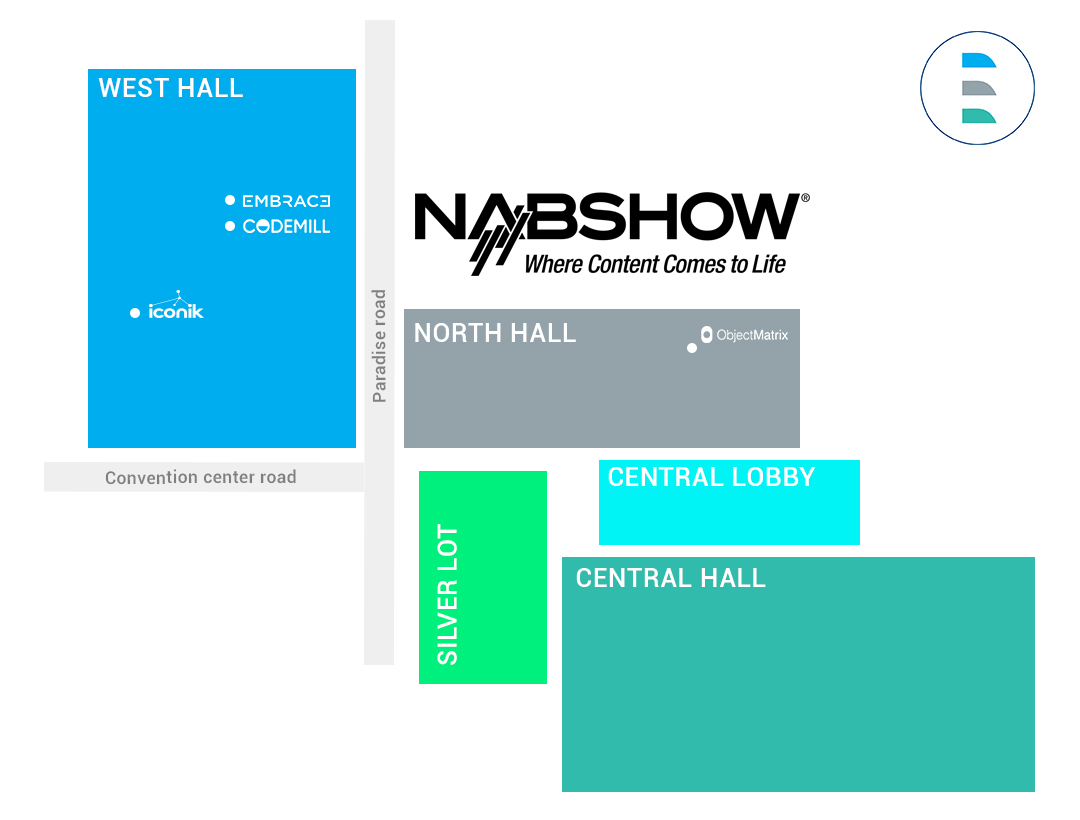
Stand W2434
By understanding customers, users, and workflows within the media supply chain, Codemill provides enjoyable and efficient solutions to best fit their needs, Accurate.Video and Cantemo. They do this by providing media workflow applications that enable M&E companies to save time and money employees enjoy their workday and tools.
Stand W2335
Stop repetitive work. Embrace designs user-centric systems that simplify complex media workflows to help leading media groups internationally to streamline their operations, empower their best creative talents and enhance the overall quality of their work.
Stand W3157
iconik allows organizations to securely manage and share their media, collaborate on projects, and create the most iconik work ever; whether you’re working alone or as part of a global team.
Stand N2965A
Pioneers of object storage and media archives modernization, Object Matrix enables global collaboration, increase operational efficiencies, and empower creativity through deployment of MatrixStore, the on-prem, hybrid and cloud storage platform. It brings operational and financial benefits to customers by securely managing content at every stage of its lifecycle.
Follow us
Follow us
Short headline
Change the color to match your brand or vision, add your logo, choose the perfect layout, modify menu settings and more.
Who is Codemill?

IVORY now represents Codemill in Belgium, Spain, France, and Luxembourg.
Let’s talk a bit about Codemill, but first, a bit of history:
Codemill, established in 2007 and located in Umeå in northern Sweden, is a leading full stack developer for custom software for the media and entertainment industry. Codemill supports audiovisual professionals in user interface customization to make their workflows fluid and is the editor of two technological solutions in media management:
– Accurate.Video
– Cantemo
– Digital Services (UI/UX)
Accurate.Video is a cloud-native product suite for content preparation. It allows the operational staff to view their media and make quick changes. Videos, sounds and metadata are brought together in a single interface to simplify business processes. It seamlessly integrates with video, app, and MAM platforms.
Within the Accurate.Video suite, Accurate.Player is a professional web browser-based video, audio and subtitle media player. It is particularly advantageous because it allows being accurate to the frame.
Cantemo offers a next generation media management service. Cantemo is leading the revolution in modern media asset management that keeps you in control of all your media content, regardless of industry or size.
Three case studies via this link.
Digital Services (UI/UX) contributes to the user experience by delivering a personalized interface.
Do not hesitate to visit the Codemill website for more information.
Follow us
Follow us
Protect and secure your audiovisual heritage

CYBERCRIMINALITY: How to fight against daily attacks and protect my audiovisual heritage?
In April 2015, the Twitter and Facebook accounts, as well as the TV5MONDE website were hacked shortly before 10 p.m. The hackers claimed to be from the Islamic State group and spread their propaganda messages through these channels before the accounts were taken over. It was the first significant cyberattack in France. At that time, large media companies suffered a few daily attacks whereas now they number in the thousands.
This year, the American group Sinclair Broadcast counts up to 20,000 attacks per day. In 2020, it was the M6 group suffered a cyber-attack. The observation: the media are targeted by cybercriminals. It is in this context towards cyber risks that we organized a round table at SATIS 2022 on this subject. Here is our report.
During this meeting, we shared best practices in terms of data accessibility, secure remote work and hybrid-cloud storage.
1) HUMAN NEGLIGENCE
Media insecurity is mostly caused by human error, cybercriminals, technical problems, or natural disasters. Human negligence being number 1, poor management of your media can constitute a cyberthreat on its own, and can serve as a ricocheting doorway for cybercriminals.
While the market is changing, broadcasters must simultaneously train and educate their users since attacks generally occur because of errors by internal collaborators. Also, freelancers are sometimes overlooked in the training process despite their major role in the supply chain.
2) AUTORISATION AND ACCESS TO DATA
It is important to have a data access policy and to identify the levels of rights and define the audiences authorized to view, modify, or delete your media.
Be sure to adapt the level of training and awareness of your teams so that they are aware of the flaws and can act accordingly. The risk is all the greater when you use a hybrid-cloud solution where content can be accessed without restriction. Several tools can be put in place to meet this challenge:
- Logins (username and password)
- Watermarks
- Permission levels
- The use of a Media Asset Management
- Or an application developed internally
It is advisable to have a “zero-trust” approach. Don’t trust anyone, internally or externally. A single infection in the supply chain can impact production, service providers and distribution.
3) PERMANENT AUDITS
Audits provide visibility into who is accessing my content, who is using it, how and when. It is an effective solution to identify a problem or unusual use and solve it more easily.
In summary, to protect against cyberattacks:
- Install firewalls/antivirus
- Define conditions for transferring media via the cloud
- Build a data access policy
- Set up identification tools
- Train and sensitize your teams
No script is written. Considering all possibilities remains the key to dealing with cyberattacks.
READ: Mediakwest article
Follow us
Follow us
IVORY and its partners will attend SATIS 2022

IVORY and its partners will attend SATIS 2022
On November 9 and 10, the French-speaking media, entertainment and audiovisual communication industry will meet at SATIS 2022, at the Docks de Paris.
IVORY will be present to discuss and support visitors in their digital transformation challenges, in under 3 formats.
EXHIBITION
As a key player of the media engineering sector, we select and support new entrants in a complex European market. As part of this function, Codemill, Embrace, iconik and Object Matrix will be exhibiting at SATIS.

CONVERSATIONS
Protect and secure your audiovisual heritage
Wednesday, November 9 from 10:30 a.m. to 11:30 a.m.
With ever more contributors, stakeholders, and distribution opportunities, how can you ensure the safety and security of your media throughout their life cycle?
Effectively reuse and monetize your media catalog
Wednesday, November 9 from 3:00 p.m. to 4:00 p.m.
For news, streaming and sports, it has become imperative to access their media in real time. What are the obstacles that remain and what can be the solutions to strengthen their effectiveness?
AWS, a potential threat for software vendors?
Thursday, November 10 from 10:30 a.m. to 11:30 a.m.
Giants, such as Amazon Web Services, place research and development at the heart of their strategy to be ever more innovative. Should we worry about specialized software vendors who deal with very specific business issues?
COCKTAIL
Wednesday November 9 from 6:00 p.m.
The opportunity to meet our team of experts and discuss your challenges.
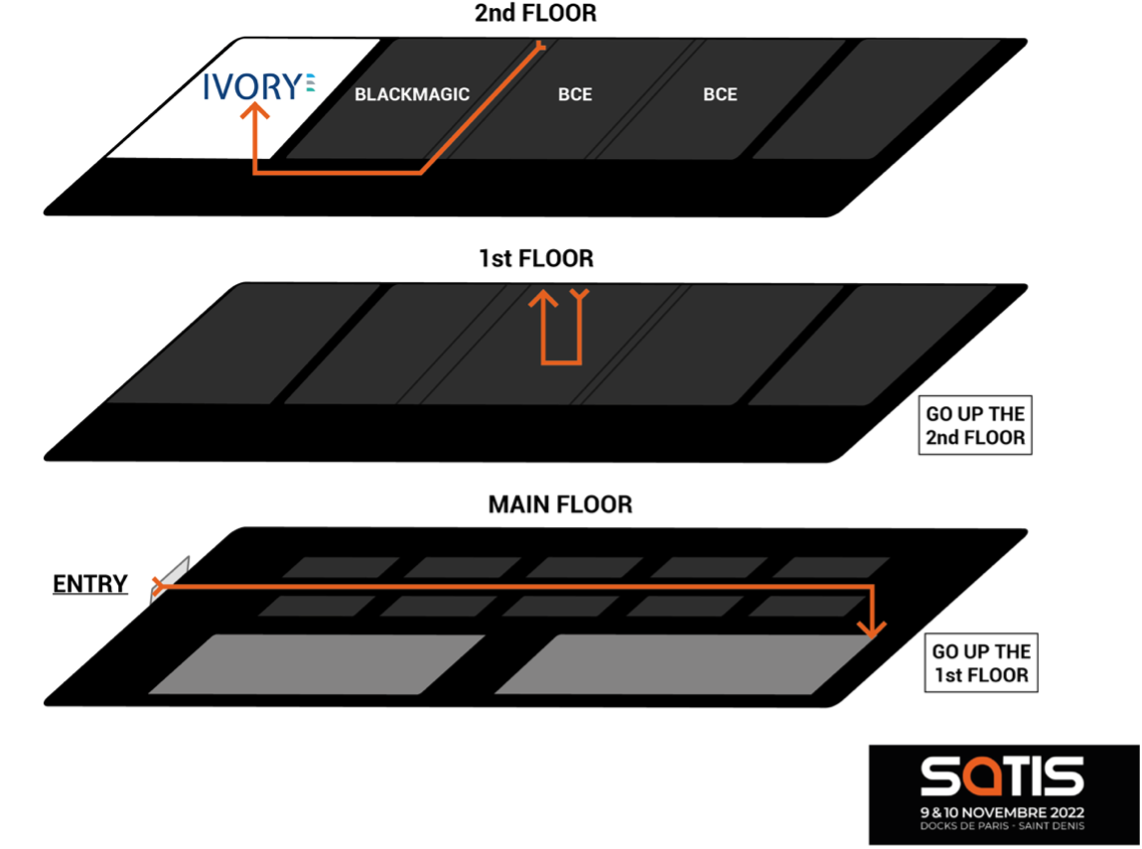
All meetings will take place in the conference area, on the 2nd floor –IVORY room.
PARTNERS
By understanding customers, users, and workflows within the media supply chain, Codemill provides enjoyable and efficient solutions to best fit their needs, Accurate.Video and Cantemo. They do this by providing media workflow applications that enable M&E companies to save time and money employees enjoy their workday and tools.
Stop repetitive work. Embrace designs user-centric systems that simplify complex media workflows to help leading media groups internationally to streamline their operations, empower their best creative talents and enhance the overall quality of their work.
iconik allows organizations to securely manage and share their media, collaborate on projects, and create the most iconik work ever; whether you’re working alone or as part of a global team.
Pioneers of object storage and media archives modernization, Object Matrix enables global collaboration, increase operational efficiencies, and empower creativity through deployment of MatrixStore, the on-prem, hybrid and cloud storage platform. It brings operational and financial benefits to customers by securely managing content at every stage of its lifecycle.
Follow us
Follow us